In Bad Passwords part 1, we talked about common and weak passwords.So what makes a password “strong”?
If you really get into it, that is a surprisingly tricky question.
So, we’ve all seen it a million times – when you sign up for something online and they ask you to make a password of at least 8 digits, a mix of upper and lowercase letters and some sort of $pecial ch@racters. That’s it right? That’s all you need?
Well – yes and no. That will make an okay password, one that is way better than the passwords we looked at in Bad Passwords part 1.
But is it really strong? Probably not. Why is that? It starts with the differences in how people and computers think, and the different attacks hackers have at their disposal. The best passwords need to be hard for both humans and computers to guess.
People need to remember passwords, and when faced with trying to come up with a new password, our minds tend to go in similar directions.
In 2011, Troy Hunt analyzed how people choose passwords. He found that:
- 14% of passwords are based on a name
- 8% are based on place names
- 25% are based on dictionary words (password, monkey, dragon)
- 14% are numeric, most being variants on 123456789 or strings of the same number 111111, 000000, 11223344, 111222333
- Less common but notable, about 3% are double words (lovelove, poopoo)
- About 3% reuse the beginning of their email address
- Also common are very short phrases (iloveyou, trustno1, letmein), keyboard patterns (qwerty, 1q2w3e, qazwsx), and pop culture references (starwars, naruto)
He concluded that:
- Passwords are inspired by words of personal significance or other memorable patterns.
- Attempts to obfuscate or strengthen passwords usually follow predictable patterns.
- Truly random passwords are all but non-existent – they’re less than 1% of the data set.
A quick look at NordPass’ 200 most used passwords of 2021 list shows that ten years later, all of these patterns continue to hold true.
Hackers know this, and they tailor their attacks to match.
This brings us around to the types of attacks used and what that means for password strength. First, let’s talk about a brute force attack. This amounts to computers trying every possible combination until they land on the right one. How long that takes is a combination of computing power, the length of the password, and all the available characters one can use to make up the password. For example, a six-digit code using only numbers 0-9 has ten possible choices for each digit, so 10x10x10x10x10x10=1,000,000 possible combinations. Compare that to a twelve-digit code that can use upper and lower case letters, the ten numbers and ten special characters, you now have 72 possible options over 12 digits, or 19,408,409,961,765,342,806,016 possible combinations. Clearly one of those would take a LOT longer to break by brute force. (Read this for more about password mathematics.)
As long and complex as that is, computers are shockingly fast. In 2012, a specialized computer cluster was able to make 350 billion guesses per second – fast enough to brute force every possible eight-digit combination of upper and lower case letters, numbers, and symbols in less than six hours.
Even so, hackers will tell you that brute force is not their first choice. They know what you and I know about how people make passwords, and have developed dictionary attacks. Dictionary attacks will compare passwords to lists of common and leaked passwords, names, common words and phrases, place names, and common variants like a 1 or ! added to the end of those words.
In short, they look for exactly the kind of passwords people tend to make.
So, how do I make my password stronger?
There’s several approaches you can take to make a stronger password., some of which don’t even involve passwords. Here’s some things to try:
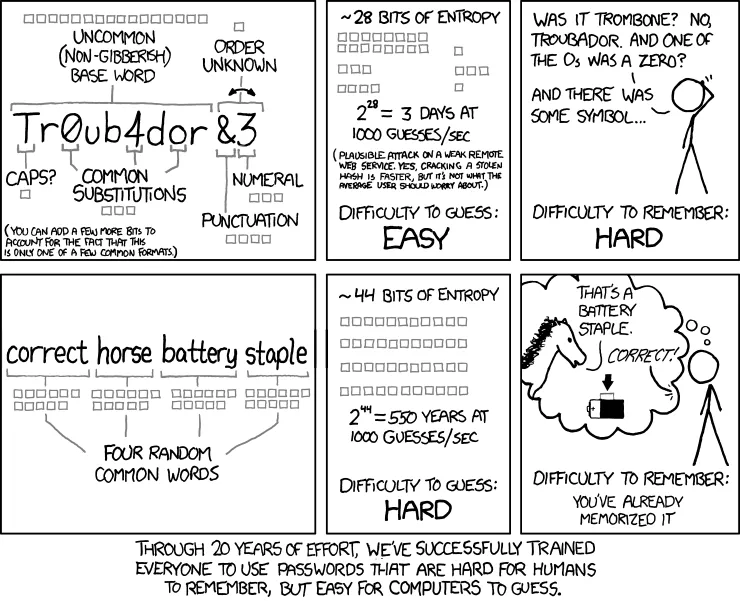
Instead of a password, try a passphrase
Made famous in internet comic XKCD, passphrases are becoming a favorite of many in the security community, even the FBI.
The strength of the passphrase lies mainly in its length. They can be very long, yet are so much easier for humans to remember. The main things to remember when using a passphrase are to not make your phrase too short or too common, like common catchphrases, or names of movies or songs – or a dictionary attack could make quick work of it.
Use a Password Manager program, and let it pick out long, random passwords for you.
We highly recommend doing this – the longer and more random and impossible to remember your passwords are, the better! A good password manager can take care of all of that for you.
Use Two-Factor Authorization whenever possible.
Sure, having to enter a code texted to you is annoying, and doesn’t work well for shared accounts, but if that data is important – like banking information – the extra layer of security is definitely worth the extra time and effort.
If you must use a not-random password, mix it up.
Now you know what not to do in a password, don’t do it! If possible, make yours at least 12 characters long. Add your capitals, numbers and symbols in unpredictable places, not at the beginning or the end. Avoid names, places, sports teams, common phrases and pop culture references. Most of all, don’t reuse old passwords, or obvious variants on them, like we talked about above. If that old password was leaked at any time, it’s on a dictionary attack password list somewhere, and will be that much more vulnerable to attack.